Introduction To Modern Cryptography
本文最后更新于 2022年11月21日 晚上
Introduction To Modern Cryptography 这本书英文原版的前两章笔记
Introduction To Modern Cryptography
Introduction and Classical Cryptography
Introduction
The Setting of Private-Key Encryption
-
The syntax of encryption
- message space: M
- three algorithms:
- Gen
- key space: K
- Enc
- Dec
- Gen
- for every key k output by Gen and every message , it holds that .
-
Keys and Kerckhoff’s principle
The cipher method must not be required to be secret, and it must be able to fall into the hands of the enemy without inconvenience.
- It is significantly easier for the parties to maintain secrecy of a short key than to keep secret the algorithm they are using.
- it will be much easier for them to change a key than to replace an encryption scheme.
- for large-scale deployment it is significantly easier for users to all rely the same encryption algorithm.
Historical Ciphers and Their Cryptanalysis
-
Caesar’s cipher: shift the letters of the alphabet
- ROT-13 is still used nowadays, merely used to ensure the text is unintelligible.
-
Sufficient key-space principle
Any secure encryption scheme must have a key space that is sufficiently large to make an exhaustive-search attack infeasible.
- this is only true if the message space is larger than the key space.
-
The mono-alphabetic substitution cipher
- attack relies on average letter frequencies
-
The Vigenere(poly-alphabetic shift) cipher
- the character frequencies are “smoothed out”
- attack: tabulate the frequency of each ciphertext character for each stream; Kasiski’ method; index of coincidence method
Principles pf Modern Cryptography
Principle 1 , Formal Definitions
-
a threat model & a security goal
-
An example: secure encryption
- Wrong answers
- it should be impossible for an attack to recover the key.
- it should be impossible for an attack to recover the entire plaintext from the ciphertext.
- it should be impossible for an attacker to recover any character of the plaintext from the ciphertext.
- Right answer
- regardless of any information an attacker already has, a ciphertext should leak no additional information about the underlying plaintext.
- Wrong answers
Principle 2 , Precise Assumption
- Reasons
- mathematical proofs require this
- Validation of assumptions
- Comparison of schemes
- Understanding the necessary assumptions
Principle 3 , Proofs of Security
Perfectly Secret Encryption
-
Generating randomness:
- collect a “pool” of high-entropy data
- process the data to yield a sequence of nearly independent and unbiased bits
-
rand() function in the C library is not cryptographically secure.
Definitions
-
perfectly secret
An encryption scheme with message space is perfectly secret if for every probability distribution over , every message , and every ciphertext for which :
-
an equivalent formulation of perfect secrecy
For every , and every , .
-
The adversarial indistinguishability experiment
- The adversary outputs a pair of messages .
- A key is generated using Gen, and a uniform bit is chosen. Ciphertext is computed and given to . We refer to as the challenge ciphertext.
- outputs a bit .
- The output of the experiment is defined to be 1 if , and 0 otherwise. We write if the output of the experiment us 1 and in this case we say that succeeds.
-
Perfectly indistinguishable
Encryption scheme with message space is perfectly indistinguishable if for every it holds that
-
Encryption scheme is perfectly secret if and only if it is perfectly indistinguishable.
The One-Time Pad
- The one-time pad encryption scheme is perfectly secret.
- The key is as long as the message.
- The same key can be used only once.
Limitations of Perfect Secrecy
- If (Gen, Enc, Dec) is a perfectly secret encryption scheme with message space and key space , then .
Shannon‘s Theorem*
-
Shannon’s theorem
Let (Gen,Enc,Dec) be an encryption scheme with message space , for which . The scheme is perfectly secret if and only if:
- Every key is chosen with equal probability by algorithm Gen.
- For every and every , there exists a unique key such that outputs c.
※:The theorem only applies` when
Private-Key (Symmetric) Cryptography
Private-Key Encryption
Computational Security
- Computational security incorporates two relaxations relative to information theoretic notions of security
- Security is only guaranteed against efficient adversaries that run for some
feasible amount of time. - Adversaries can potentially succeed with some very small probability.
- Security is only guaranteed against efficient adversaries that run for some
The Concrete Approach
- A scheme is -secure if any adversary running for time at most t succeeds in breaking the scheme with probability at most .
The Asymptotic Approach
-
A scheme is secure if any ppt adversary succeeds in breaking the scheme with at most negligible probability.
-
A function f from the natural numbers to the non-negative real numbers is negligible if for every positive polynomial there is an such that for all integers it holds that .
- and are negligible functions. Then,
- is negligible.
- is negligible.
- and are negligible functions. Then,
Necessity of the Relaxations
- If we wish to encrypt many messages using a single short key, security can only be achieved if we limit the running time of the adversary.
Defining Computationally Secure Encryption
- A private-key encryption scheme is a tuple of probabilistic polynomial-time algorithm (Gen, Enc, Dec) such that:
- The Gen takes as input and outputs a key ; we write . We assume without loss of generality that any key output by satisfies .
- The Enc takes as input a key and a plaintext message , and output a ciphertext . Since Enc may be randomized, we write this as .
- The Dec take as input a key and a ciphertext , and outputs a message or an error. We assume that Dec is deterministic, and so write . We denote a generic error by the symbol .
The adversarial indistinguishability experiment
- The adversary is given input , and outputs a pair of messages with .
- A key is generated by running , and a uniform bit is chosen. Ciphertext is computed and given to . We refer to as the challenge ciphertext.
- outputs a bit
- The output of the experiment is defined to be 1 if , and 0 otherwise. If , we say succeeds.
Indistinguishable encryption in the presence of an eavesdropper/EAV-secure
- Definition 1: For all probabilistic polynomial-time adversaries there is a negligible function such that, for all , .
- Definition 2: For all PPT adversaries there is a negligible such that
Encryption and Plaintext Length
- Sometimes leaking the plaintext length is problematic
- Simple numeric/text data
- Auto-suggestions
- Database searches
- Compressed data
Semantic Security*
-
A private-key encryption scheme (Enc, Dec) is semantically secure in the presence of an eavesdropper if for every PPT algorithm there exists a PPT algorithm such that for any PPT algorithm Samp and polynomial-time computable functions and the following is negligible:
where the first probability is taken over uniform output by
the randomness of and the randomness of Enc, and the second probability is taken over output by and the randomness of . -
A private-key encryption scheme has indistinguishable encryptions in the presence of an eavesdropper if and only if it is semantically secure in the presence of an eavesdropper.
Constructing Secure Encryption Schemes
Pseudorandom Generators and Stream Ciphers
- For any efficient statistical test D, the probability that D returns 1 when given the output of the pseudorandom generator should be close to the probability that D returns 1 when given a uniform string of the same length.
- Pseudorandomness is computational relaxation of true randomness.
- Considering only polynomial-time observers,a pseudorandom string is just as good as a uniform string.
- Let be a polynomial and let be a deterministic polynomial-time algorithm such that for any and any input , the result is a string of length . We say that is a pseudorandom generator if the following conditions hold:
- (Expansion:) For every it holds that
- (Pseudorandomness:) For any PPT algorithm , there is a negligible function such that , where the first probability is taken over uniform choice of and the randomness of , and the second probability is taken over uniform choice of and the randomness of .
- We call the expansion of .
- Stream Ciphers: (Init, GetBits)
- Init
- Input: seed , optional initialization vector
- Output: initial state
- GetBits
- Input: state
- output: a block of several bits , updated state
Proofs by Reduction
-
A security reduction is a particular type of mathematical proof that some cryptographic primitive or protocol is secure, in the sense that it is “at least as difficult to break” as some other problem believed to be hard.
-
A proof that some cryptographic construction is secure proceeds via the following steps:
- Fix some efficient adversary attacking . Denote the 's success probability by .
- Construct an efficient algorithm , called the “reduction”, that attempts to solve problem using as a subroutine. And knows noting about how works and only knows is expecting to attack . So, given some input instance of , will simulate for an instance of such that:
- (a) As far as can tell, it is interacting with . That is, the view of when run as a subroutine by should be distributed identically to the view of when it interacts with itself.
- (b) If succeeds in “breaking” the instance of that is being simulated by , this should allow , this should allow to solve the instance is was given, at least with inverse polynomial probability
- Taken together, (a) and (b) imply that solves with probability , if is not negligible. Moreover, if is efficient then we obtain an efficient algorithm solving with non-negligible probability, contradicting the initial assumption.
- Given our assumption regarding , we conclude that no efficient adversary can succeed in breaking with non-negligible probability. Stated differently , is computationally secures.
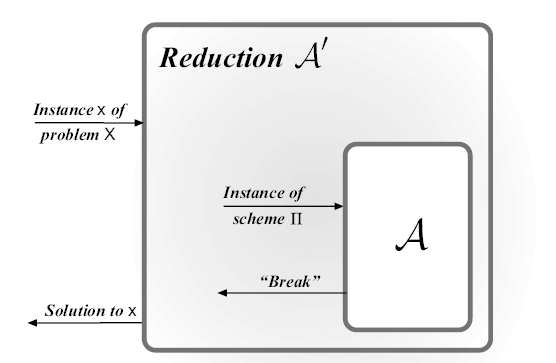
An instance for Reduction ——Distinguisher D
- D is given as input a string .
- Run to obtain a pair of messages
- Choose a uniform bit . Set
- Give to and obtain output , Output 1 if , and 0 otherwise.
Stronger Security Notions
Security for Multiple Encryptions
The multiple-message eavesdropping experiment
- The adversary is given input , and outputs a pair of equal-length lists of messages and , with for all .
- A key is generated by running , and a uniform bit is chosen. For all , the ciphertext is computed and the list is given to
- outputs a bit
- The output of the experiment is defined to be 1 if , and 0 otherwise.
Indistinguishable multiple encryptions in the presence of an eavesdropper
- For all probabilistic polynomial-time adversaries there is a negligible function such that .
※:There is a private-key encryption scheme that has indistinguishable encryption in the presence of an eavesdropper, but not indistinguishable multiple encryption in the presence of an eavesdropper. For example: the encryption scheme is deterministic.
Chosen-Plaintext Attacks and CPA-Security
- encryption oracle: a “black box” that encrypts messages of ’s choice using a key that is unknown to . can interact with the oracle as many times ad it likes and query the reply of the oracle.
The CPA indistinguishability experiment
-
A key is generated by running .
-
The adversary is given input and oracle access to , and outputs a pair of messages of the same length.
-
A uniform bit is chosen, and then a ciphertext is computed and given to .
-
The adversary continues to have oracle access to , and outputs a bit .
-
The output of the experiment is defined to be 1 if , and 0 otherwise. In the former case, we say that succeeds.
CPA-secure
-
For all probabilistic polynomial-time adversaries there is a negligible function such that .
-
Any private-key encryption scheme that is CPA-secure is also CPA-secure for multiple encryptions.
Constructing CPA-Secure Encryption Schemes
-
Pseudorandom function: Let be an efficient, length-preserving, keyed function. is a pseudorandom function if for all probabilistic polynomial-time distinguishers , there is a negligible function such that: .
- size: