2021 红明谷 Misc Writeup
本文最后更新于 2025年12月28日 晚上
2021 “红明谷”杯数据安全大赛 Misc Writeup
2021 红明谷 Misc Writeup
inputMonitor
-
题目描述:Akira在某次取证的过程中,在桌面找到了一个奇怪的文件,但是除此之外好像没有找到什么有价值的情报,很多的数据都被抹干净了,而且这个用户似乎根本就没装什么第三方的软件。Akira还粗心的只拷贝了C盘下的User目录,这下还有机会解开可疑文件吗?
-
提供了打包的 User 目录
-
解法
- 利用脚本清理一下空文件,方便人工查找需要的新信息
1
2@echo off
for /f "tokens=*" %%i in ('dir/s/b/ad^|sort /r') do rd "%%i"- 发现
Dump_6e7e51d82aa230fe12d1fbc145da6441\User\link3\Desktop里面有flag.7z和log_data.txt。- flag.7z:需要密码,或许得到了密码就能获得 flag
- log_data.txt:显示
没事,我都删掉了,之前的聊天记录都被我清干净了。除非他们在监控我输入,综合题目名称,猜测应该需要分析输入记录
- 考虑输入法的记录,参考输入法取证:一种Windows8/10中文用户输入痕迹信息提取方法研究与实现
- 与中文输入法相关的用户词库文件主要存储在
C:\Users\Administrator\AppData\Roaming\Microsoft\InputMethod\Chs中ChsPinyinlH.dat文件记录着系统用户的中文字词输入信息ChsPinyinUDL.dat文件记录着系统用户的中文短句输入信息
- 利用 微软拼音自学习词库的导入导出算法中 @HowcanoeWang 的脚本,就能获得输入记录。
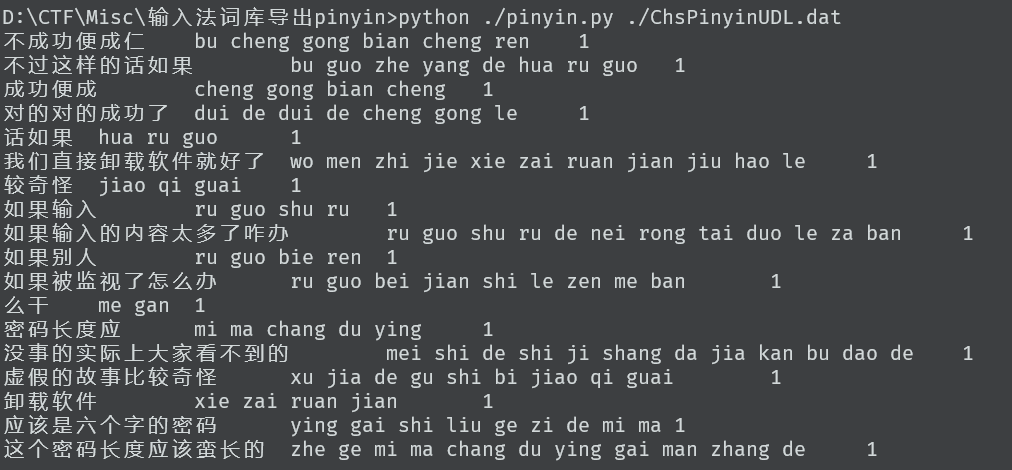
- 与中文输入法相关的用户词库文件主要存储在
- 密码是:
有志者事竟成- 解压得到一个 pdf 文件
- 解压得到一个 pdf 文件
- 删除图片,得到图片下的 flag
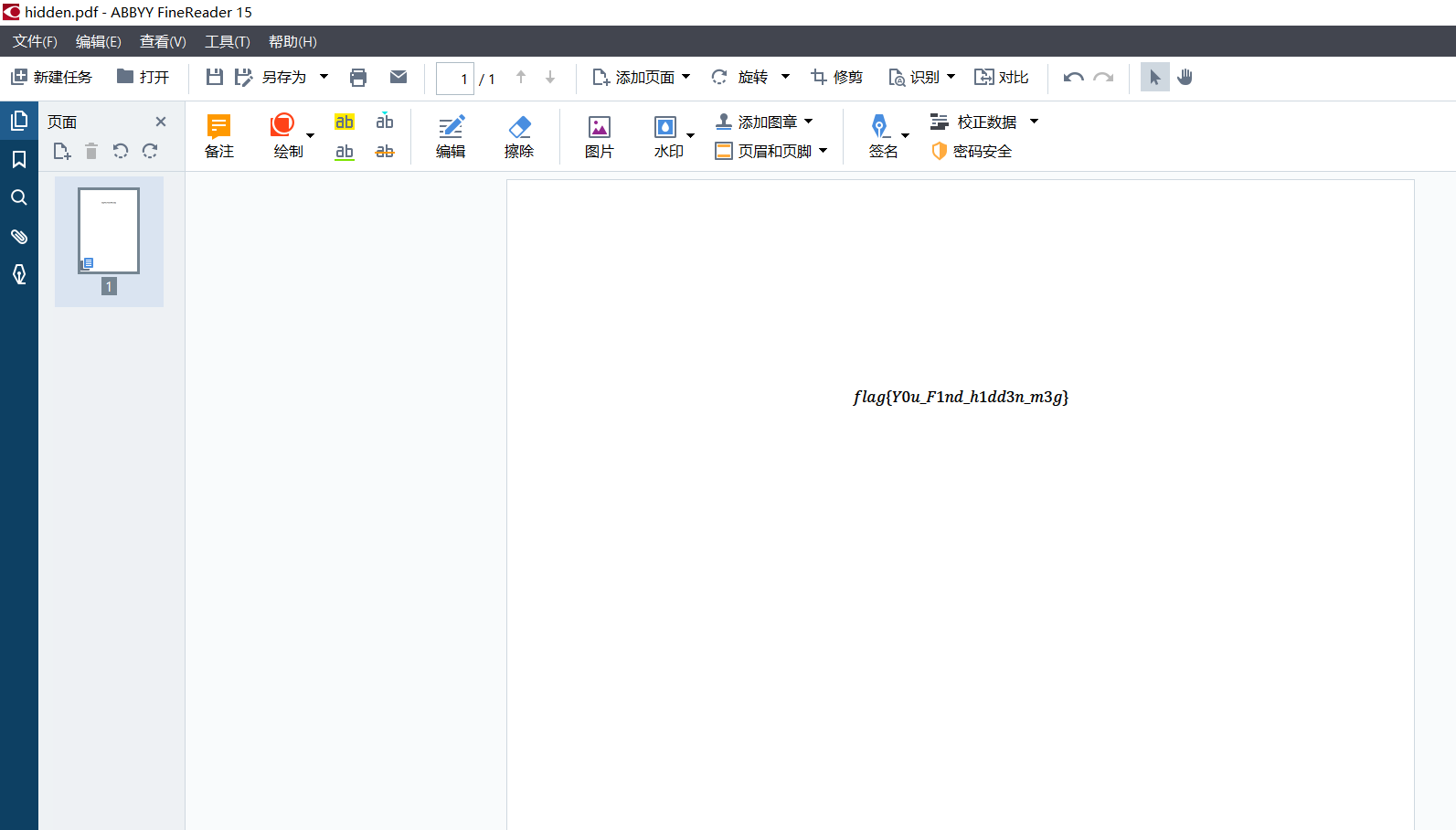
快用你那无敌的取证大师想想办法啊!
然而,我使用取证大师并没有分析出结果
我的心是冰冰的
- 题目描述:似乎有信息被隐藏了。
- 提供一个压缩包
- 解法
-
用 WinRAR 打开就报错,解压还需要密码……应该是使用了伪加密——然而,一般伪加密不是对于ZIP而言的么?
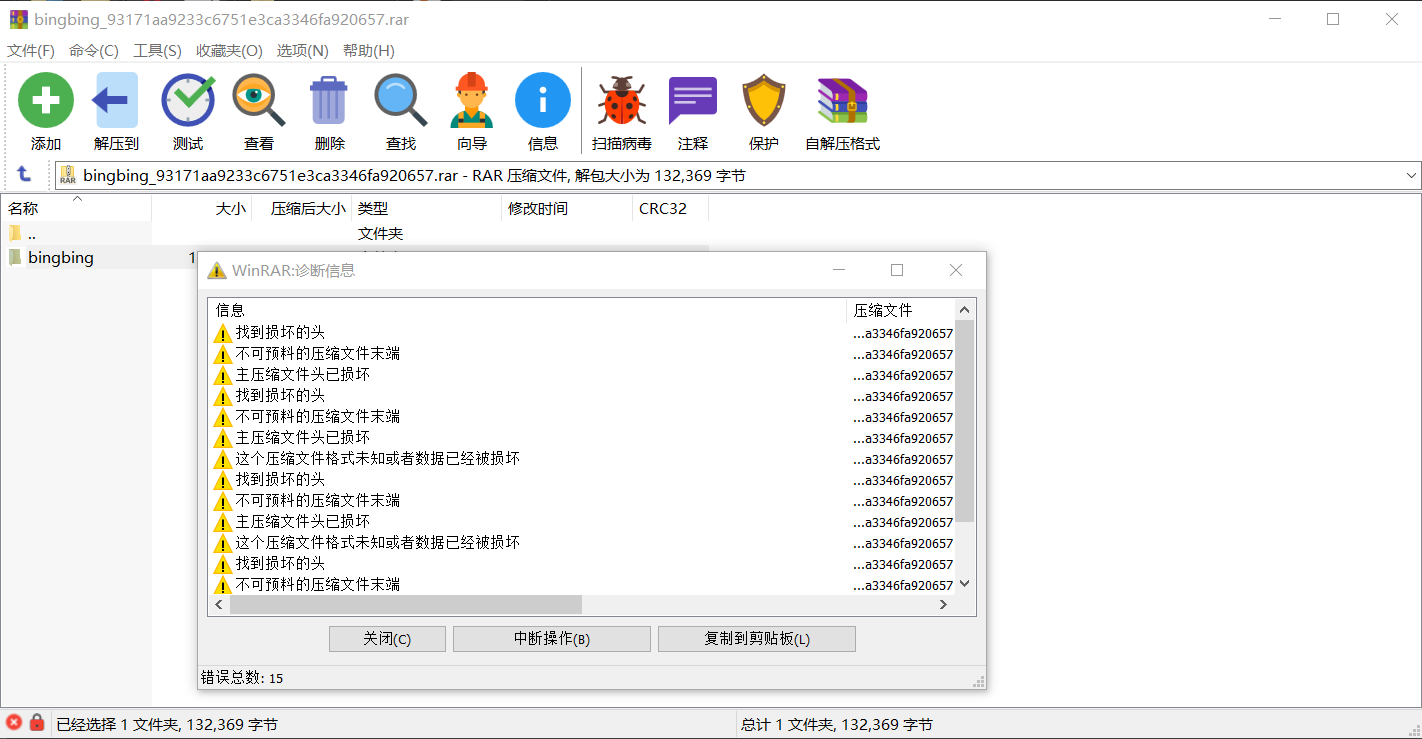
- 看了L1near 师傅的官方 writeup 后,需要修改 RAR 第 24 字节处(对应
PASSWORD_ENCRYPTED)从1改为0就可以正常打开文件了/把第24字节的后面一个4改成0也可以 - 然而,即便是使用了 010editor 的模板也没有解析处这里对应
PASSWORD_ENCRYPTED,看官方 writeup 应该是 RAR 版本问题 - 但是,或许正因为是版本问题,我在没有做任何伪加密修改时,同样能够正常解压缩
- 看了L1near 师傅的官方 writeup 后,需要修改 RAR 第 24 字节处(对应
-
解压得到
bingbing.jpg和bingbing.zipbingbing.zip有密码,含有一个bingbing.pcapng文件
-
根据官方 writeup,这是简单 FFT,其 payload 如下:(然而这道题改了,这样跑不出结果)
1
2
3
4
5
6
7
8
9
10
11
12
13
14import cv2 as cv
import numpy as np
import matplotlib.pyplot as plt
img = cv.imread('FFT.png', 0) #直接读为灰度图像
f = np.fft.fft2(img) #做频率变换
fshift = np.fft.fftshift(f) #转移像素做幅度谱
s1 = np.log(np.abs(fshift))#取绝对值:将复数变化成实数取对数的目的为了将数据变化到0-255
plt.subplot(121)
plt.imshow(img, 'gray')
plt.title('original')
plt.subplot(122)
plt.imshow(s1,'gray')
plt.title('center')
plt.show()- 这里需要使用 Java 盲水印:
1
java -jar .\BlindWatermark.jar decode -c .\bingbing.jpg clue.jpg- Java 盲水印的工具:BlindWatermark


-
得到压缩包密码:
gnibgnib -
打开压缩包,获得
bingbing.pcapng
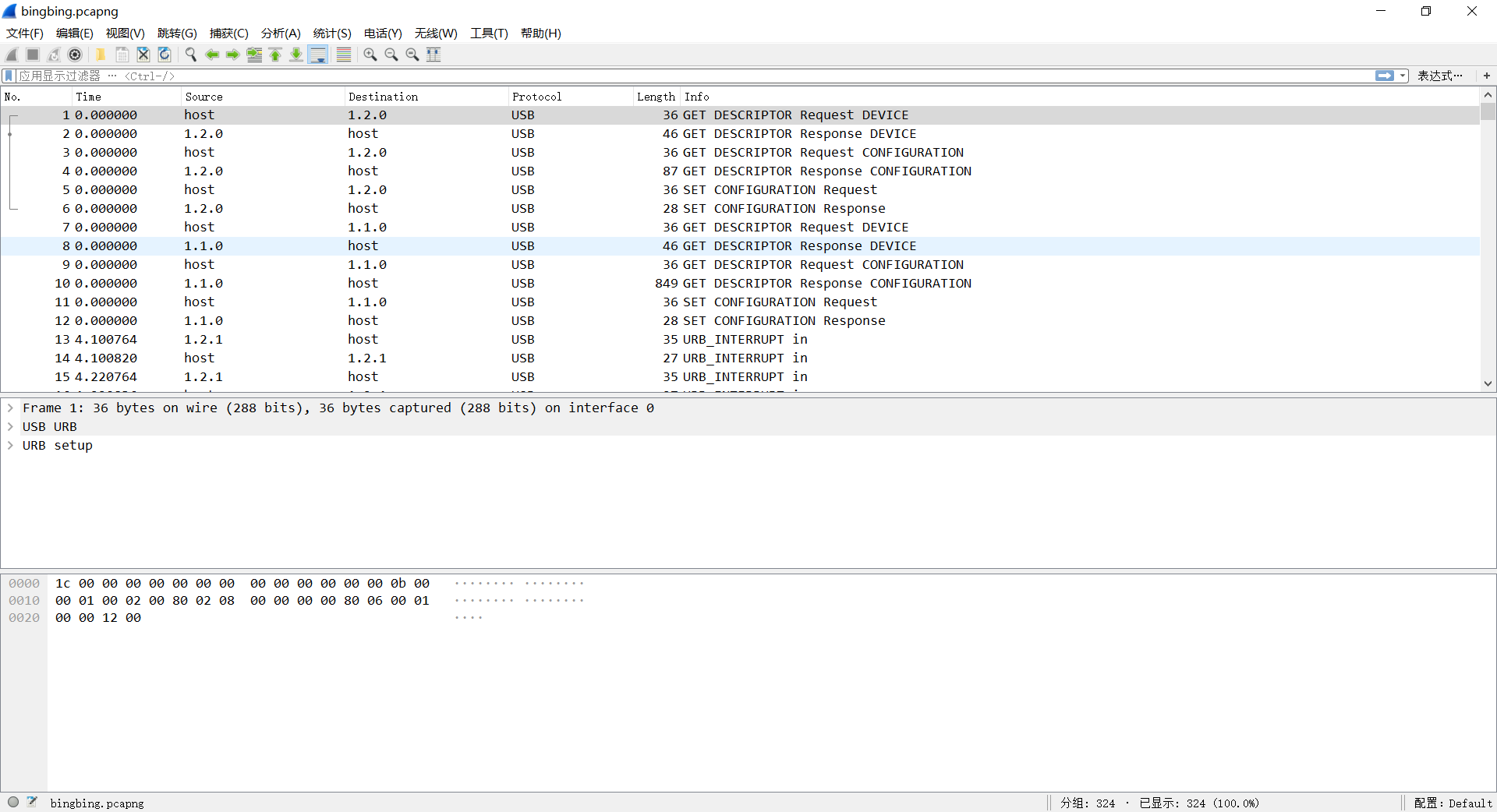
-
USB键盘流量,使用 tshark + USB Keyboard Data Hacker 得到
666c61677b38663965643266393333656631346138643035323364303334396531323939637d -
Hex 转 ascii 得到flag
-
歪比歪比
-
题目描述:戴夫发送了一些信息给僵尸,但是被我截获到了。看看能从里边发现什么?好像是一个Surprise,你来翻译翻译?
-
提供一个名为
data的文件- 实际上是一个 pcap 包(利用Online TrID)
-
解法
- 追踪TCP流,得到如下文本
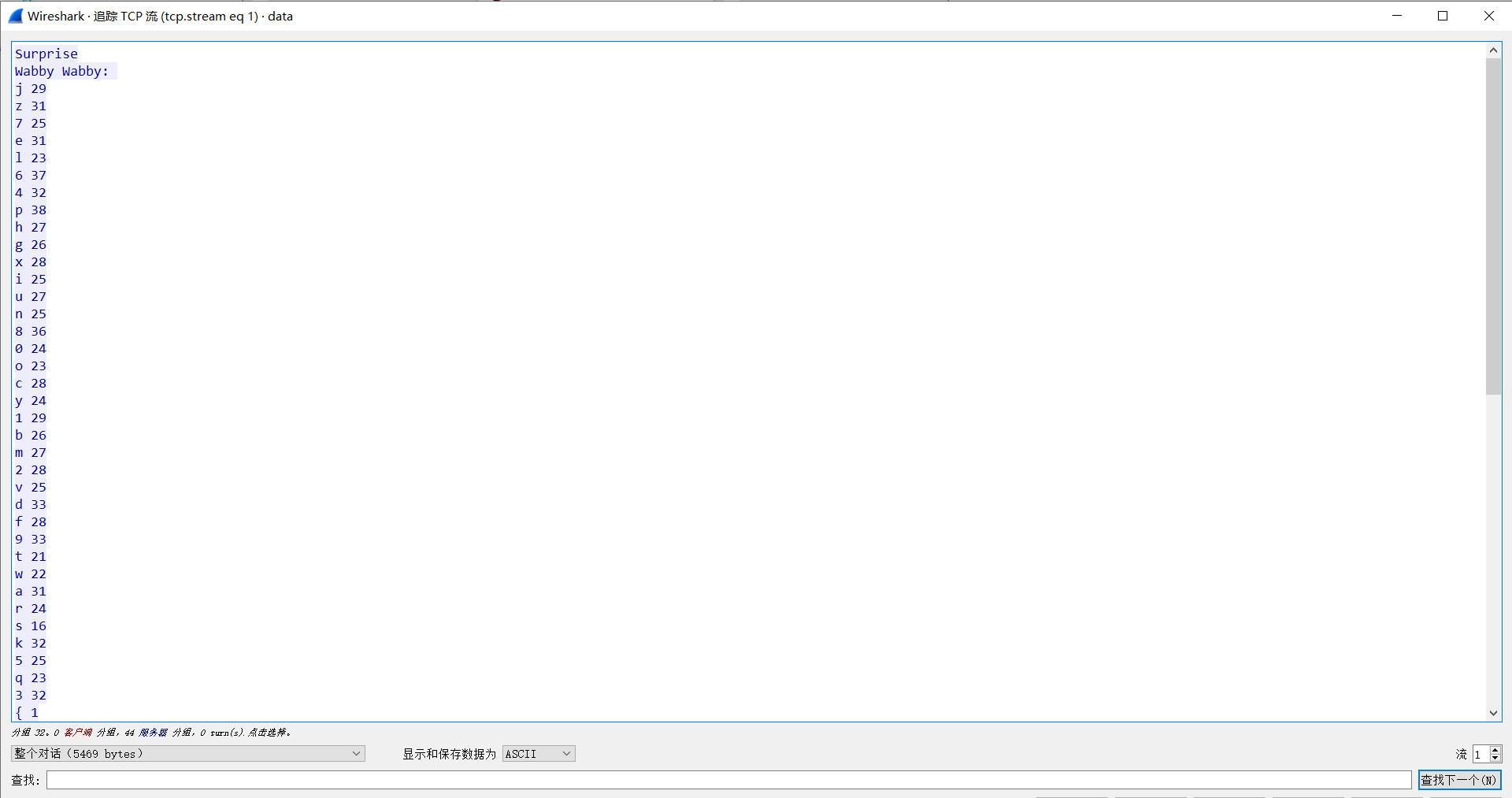
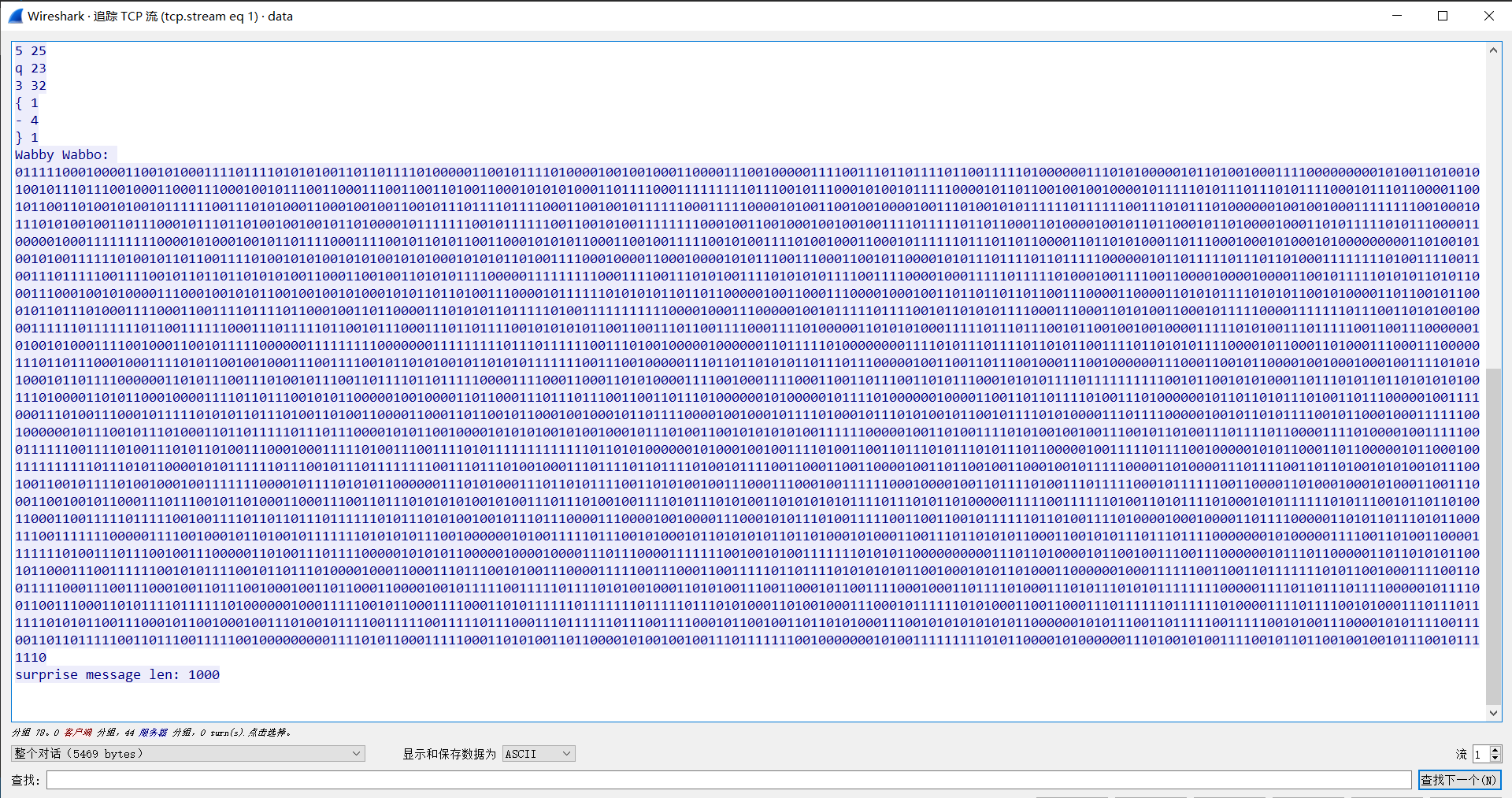
- 明显是词频统计,哈夫曼编码
- payload如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149# 统计字符出现频率
def countFrequency(text):
chars = []
chars_freqs = []
for char in text:
if char in chars:
continue
else:
chars.append(char)
chars_freqs.append((char, text.count(char)))
return chars_freqs
# 节点类
class Node:
def __init__(self, freq):
self.left = None
self.right = None
self.father = None
self.freq = freq
def isLeft(self):
return self.father.left == self
# 根据freqs数组创建叶子节点
def createNodes(freqs):
return [Node(freq) for freq in freqs]
# 构建Huffman树
def createHuffmanTree(nodes):
queue = nodes[:]
while len(queue) > 1:
queue.sort(key=lambda item: item.freq)
node_left = queue.pop(0)
node_right = queue.pop(0)
node_father = Node(node_left.freq+node_right.freq)
node_father.left = node_left
node_father.right = node_right
node_left.father = node_father
node_right.father = node_father
queue.append(node_father)
queue[0].father = None
return queue[0]
# 由Huffman树得到Huffman编码
# codes,nodes,chars_freqs的下标是一一对应的
def encodeHuffman(nodes, root):
codes = ['']*len(nodes)
# 对于每一个节点,找其父节点,若其父节点是左侧节点,则编码前添加'0'
# node_tmp即用于一层层向上寻找父节点
for i in range(len(nodes)):
node_tmp = nodes[i]
while node_tmp != root:
if node_tmp.isLeft():
codes[i] = '0'+codes[i]
else:
codes[i] = '1'+codes[i]
node_tmp = node_tmp.father
return codes
# 编码字符串
def encodeStr(text, chars_freqs, codes):
huffmanStr = ''
# 对字符串中的每个字符,遍历chars_freqs,查看对应codes的下标
for char in text:
for i in range(len(codes)):
if char == chars_freqs[i][0]:
huffmanStr += codes[i]
break
return huffmanStr
# 解码哈夫曼编码串
def decodeStr(huffmanStr, chars_freqs, codes):
orignStr = ''
# 利用截断的方法,每次截取哈夫曼编码首部
while huffmanStr != '':
# 遍历codes,查看是否有codes在哈夫曼编码串首部
for i in range(len(codes)):
if codes[i] in huffmanStr and huffmanStr.index(codes[i]) == 0:
orignStr += chars_freqs[i][0]
huffmanStr = huffmanStr[len(codes[i]):]
return orignStr
if __name__ == '__main__':
trash_array = {
'j': 29,
'z': 31,
'7': 25,
'e': 31,
'l': 23,
'6': 37,
'4': 32,
'p': 38,
'h': 27,
'g': 26,
'x': 28,
'i': 25,
'u': 27,
'n': 25,
'8': 36,
'0': 24,
'o': 23,
'c': 28,
'y': 24,
'1': 29,
'b': 26,
'm': 27,
'2': 28,
'v': 25,
'd': 33,
'f': 28,
'9': 33,
't': 21,
'w': 22,
'a': 31,
'r': 24,
's': 16,
'k': 32,
'5': 25,
'q': 23,
'3': 32,
'{': 1,
'-': 4,
'}': 1,
}
tt = list(trash_array.items())
chars_freqs = tt
nodes = createNodes([item[1] for item in chars_freqs])
root = createHuffmanTree(nodes)
codes = encodeHuffman(nodes, root)
huffmanStr = '0111110001000011001010001111011110101010011011011110100000110010111101000010010010001100001110010000011110011101101111011001111101000000111010100000101101001000111100000000010100110100101001011101110010001100011100010010111001100011100110011010011000101010100011011110001111111110111001011100010100101111100001011011001001001000010111110101110111010111100010111011000011001011001101001010010111111001110101000110001001001100101110111101111000110010010111111000111110000101001100100100001001110100101011111101111110011101011101000000100100100011111111001000101110101001001101110001011101101001001001011010000101111111001011111100110010100111111110001001100100010010010011110111110110110001101000010010110110001011010000100011010111110101110000110000010001111111110000101000100101101111000111100101101011001100010101011000110010011111001010011110100100011000101111110111011011000011011010100011011100010001010001010000000001101001010010100111111010010110110011110100101010010101001010100010101011010011110001000011000100001010111001110001100101100001010111011110110111110000001011011111011101101000111111110100111100110011101111100111100101101101101010100110001100100110101011110000011111111100011110011101010011110101010111100111100001000111110111110100010011110011000010000100001100101111101010110101100011100010010100001110001001010110010010010100010101101101001110000101111110101010110110110000010011000111000010001001101101101101100111000011000011010101111010101100101000011011001011000101101110100011110001100111101111011000100110110000111010101101111101001111111111100001000111000001001011111011110010110101011110001110001101010011000101111100001111111011100110101001000011111101111111011001111110001110111110110010111000111011011110010101010110011001110110011110001111010000011010101000111110111011100101100100100100001111101010011101111100110011100000010100101000111100100011001011111000000111111111000000011111111101110111111001110100100000100000011011111010000000011110101110111101101011001111011010101111000010110001101000111000111000001110110111000100011110101100100100011100111100101101010010110101011111110011100100000111011011010101101110111000001001100110111001000111001000000111000110010110000100100010001001111010101000101101111000000110101110011101001011100110111101101111100001111000110001101010000111100100011110001100110111001101011100010101011110111111111100101100101010001101110101101101010101001110100001101011000100001111011011100101011000001001000011011000111011101110011001101110100000010100000101111010000001000011001101101111010011101000000101101101011101001101110000010011110001110100111000101111101010110111010011010011000011000110110010110001001000101101111000010010001011110100010111010100101100101111010100001110111100000100101101011110010110001000111111001000000101110010111010001101101111101110111000010101100100001010101001010010001011101001100101010101001111110000010011010011110101001001001110010110100111011110110000111101000010011111000111111001111010011101011010011100010001111101001110011110101111111111111011010100000010100010010011110100110011011101011101011101100000100111110111100100000101011000110110000010110001001111111111011101011000010101111110111001011101111111100111011101001000111011110110111101001011110011000110011000010011011001001100010010111110000110100001110111100110110100101010010111001001100101111010010001001111111000010111101010110000001110101000111011010111100110101001001110001110001001111110001000010011011110100111011111000101111110011000011010001000101000110011100011001001011000111011100101101000110001110011011101010101001010011101110100100111101011101010011010101010111101110101101000001111100111111010011010111101000101011111101011100101101101001100011001111101111100100111101101101110111111010111010100100101110111000011100001001000011100010101110100111110011001100101111110110100111101000010001000011011110000011010110111010110001110011111110000011110010001011010010111111101010101110010000001010011111011100101000101101010101101101000101000110011101101010110001100101011101110111100000001010000011110011010011000011111110100111011100100111000001101001110111100000101010110000010000100001110111000011111110010010100111111101010110000000000111011010000101100100111001110000001011101100000110110101011001011000111001111110010101111001011011101000010001100011101110010100111000011111001110001100111110110111101010101011001000101011010001100000010001111110011001101111111010110010001111001100111110001110011100010011011100100010011011000110000100101111100111110111101010010001101010011100110001011001111000100011011110100011101011101010111111110000011110110111011110000010111100110011100011010111101111110100000010001111100101100011110001101011111101111111011111011101010001101001000111000101111110101000110011000111011111101111110100001111011110010100011101110111111010101100111000101100100010011101001011110011111001111101110001110111111011100111100010110010011011010100011100101010101010110000001010111001101111100111110010100111000010101111001110011011011111001101110011111001000000000111101011000111110001101010011011000010100100100111011111110010000000101001111111110101100001010000001110100101001111001011011001001001011100101111110'
orignStr = decodeStr(huffmanStr, chars_freqs, codes)
print('Decode result:' + orignStr)- 运行后得到flag
- 追踪TCP流,得到如下文本
2021 红明谷 Misc Writeup
https://justloseit.top/2021 红明谷 Misc Writeup/